Sample Masters Counter Fraud and Corruption Report
Here is a sample that showcases why we are one of the world’s leading academic writing firms. This assignment was created by one of our expert academic writers and demonstrated the highest academic quality. Place your order today to achieve academic greatness.
Case Study Analysis of Insider Threat
Executive Summary
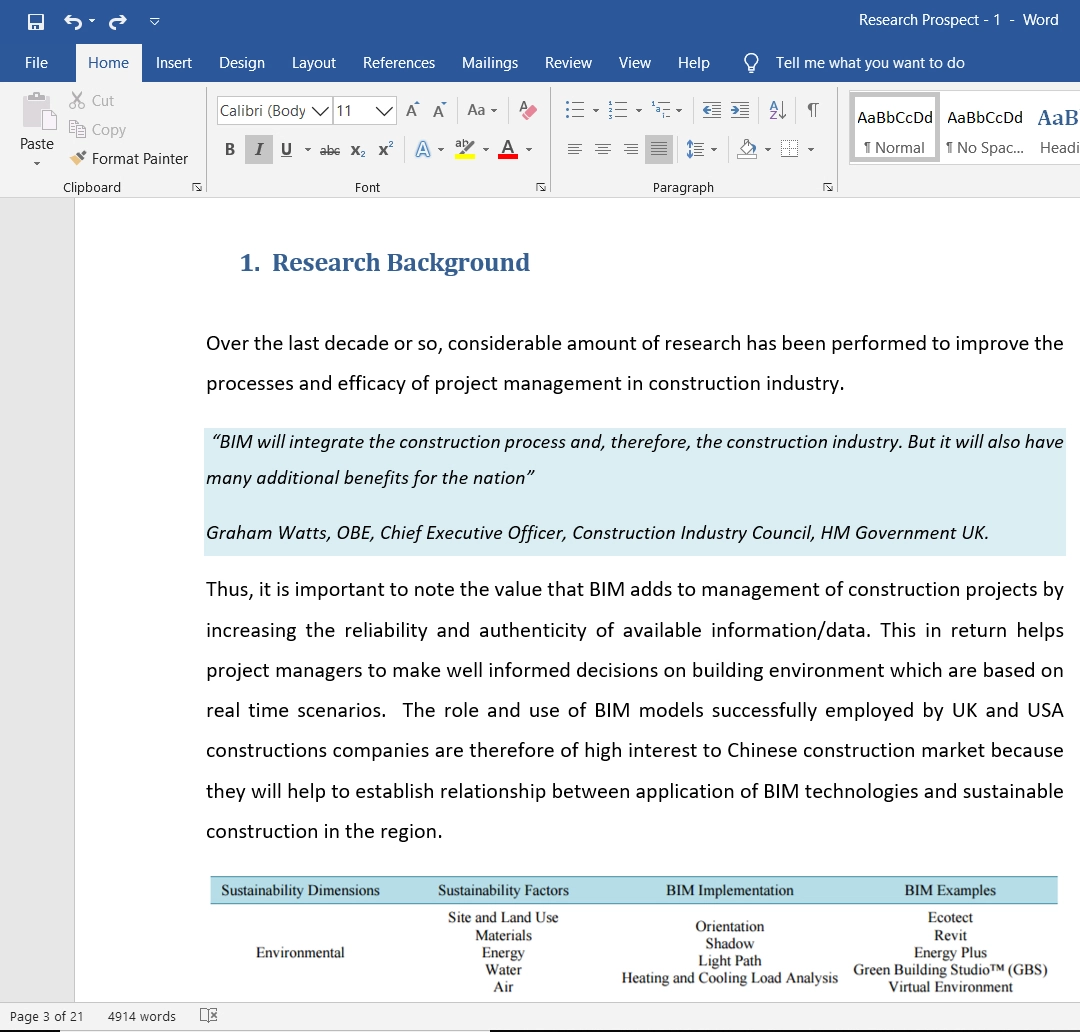
This report aims to analyse the insider threat to Inscriber Ltd. that occur due to taking a bribe for providing organisational information to others.
To attain this report’s purpose, it has found the potential causes with an evaluation of real-life cases of the companies and provides recommendations to overcome these issues.
The report’s analysis revealed that breach of customer information becomes the more profitable business in the global market.
This report identifies why increasing theft to the Business is due to misconduct and inappropriate pay structure that made the individual inclined towards unethical activities.
The report identified different types of internal threats, from employees that have malicious purposes; even those who are just trying to do their job are careless or distracted.
The reason for this activity is created by that competitors offer an irrecusable amount of money, and they will already have a spy inside the company to gain access to sensitive data such as new product launches and marketing campaigns.
To prevent the company from this threat, the audit committee is considered a powerful weapon at the disposal of organisations to effectively combat corruption.
The causes and not just the consequences of acts of corruption must be tackled. There is a myriad of audit techniques for detecting signs of corruption that are applied in Inscriber Ltd.
In the fight against corruption, the participation of all is fundamental. Reducing corruption is not an easy task. It requires continuous efforts to do monitoring and identify employees’ behavior.
Introduction
The purpose of this report is to evaluate the insider threat to Inscriber Ltd. in which the call center agents have taken a bribe from others to provide the customer’s personal information to others.
In response to this, the report will identify the key potential causes of evaluating real-life cases of the companies, and provide recommendations to overcome these issues. This report identifies the underlying reason for the occurrence of insider threats.
Moreover, the strategy recommendation has been made to avoid further internal threats to the company.
Overview
Insider threats are associated with people who have access to confidential information or an organization’s private platforms, such as employees, former employees, business partners, or service providers.
At any time in the present or past, any individual who has had access to private information and systems may represent a potential vulnerability (Wang, Gupta, & Rao, 2015).
However, not all risks related to people are promoted premeditatedly or result from fraud or industrial spying. Often, unsafe habits or lack of information about good safety practices can cause a significant number of gaps.
A user can enter an email address incorrectly when forwarding sensitive information; click links or open files in spear-phishing emails. There are still cases of browsing suspicious websites that force the download of unwanted applications, such as spyware, or promote crypto-mobile mining.
Case Analysis
Growing Customer Identity Theft
According to a survey report, a more profitable market than the global illicit drug trade is identity theft. The IT security company released a study that says that those responsible for increasing these thefts are the users themselves.
In large organisations, user misconduct accounted for 35% of incidents during the reporting period, compared to 12% in the same period last year.
Digital transformation requires new care from the digitalization that became a path for increasing efficiency. The security of the information happened to require an unprecedented level of performance.
When talking about Digital Transformation, Zargar, Nowroozi, and Jalili, (2016) indicated that the presence of technologies such as Cloud Computing, Mobility, Big Data, IoT, and social networks in the relationship between companies and their clients are generating an urgent need to redefine commercial and operational processes.
Similarly, BBC (2007) reported that data of around 15,000 customers were at risk of fraud when a customer data disk lost by the courier that contains the personal information of customers.
According to the organisation, victims worldwide lose about 290 billion dollars per year due to this type of cybercrime. In the first quarter of 2018, users increased their visits to malicious websites or installed and executed questionable software, or were still lured by e-mails and attachments from unknown senders through a phishing attack (Liu et al., 2018).
Suppose data breaches represent a high risk to affected persons. In that case, Inscriber Ltd. should inform their customer, unless there are effective technical and organisational protective measures or other measures to ensure that the risk is not realized again.
The insider attackers have some common traits as reported by CPNI: immaturity, low self-esteem, lack of ethics, higher fantasize, lack of conscientiousness, and instability (Upton, and Creese, 2014).
It is common to have different cases of a data breach by employees such as a hospital worker decides to copy patient data to a CD and publish it online. The hospital finds out what happened a few days later.
As soon as the hospital becomes aware of what happened, it has 72 hours to inform the supervisory authority since the personal data in question contain sensitive information (Suh, & Yim, 2016).
In this case, there is doubt as to whether the hospital has implemented adequate technical and organisational protection measures or not. Similarly, the employee’s data are stolen by an organisation that includes their personal information such as addresses, household composition, monthly salary, and claims for reimbursement of medical expenses of all workers.
Moreover, the leading organisation has reported cases of a data breach such as last year; Yahoo! revealed that more than one billion personal accounts were hacked from their servers (Trautman & Ormerod, 2016).
Internal Threats to the Business
There are different types of internal threats, from employees who have malicious purposes; even those who are just trying to do their job are careless or distracted. Many data breaches currently originate from internal threats or employees who have had their credentials stolen (Elhai et al., 2017).
Hence, the idea that such threats are only those employees with bad intentions looking for valuable information to sell to competitors or leaking in the press needs to be ended.
There are different types of internal threats, from employees who have malicious purposes, even those who are just trying to do their job. Management of insiders as a threat is essential for the management to ensure the quality of services and protecting the organization.
However, the organization cannot anticipate any risk due to the implementation of technology that changes the environment that affects the organization involved (Upton, and Creese, 2014).
Imagine that an employee responsible for critical processes in the company, such as the IT infrastructure, begins to feel devalued and therefore unhappy with their job (Janakiraman, Lim, & Rishika, 2018).
Another case of data theft reported by the BBC (2013) is that the policewomen were involved in gaining access to information. This activity was supported by two men who confessed their role in this activity. The case was filed against two drug dealers and the evidence was formed from the key element of prosecution.
By feeling frustrated, employees may begin to sabotage business operations on purpose. To identify this type of employee, the information security team needs to be aware of some common signs of dissatisfaction.
Employees unhappy with their salary are a problem in every Business. For a dubious competitor to win them, all managers have to offer an irrecusable amount of money. They will already have a spy inside the company to gain sensitive data such as new product launches and marketing campaigns.
According to Martin, Borah, & Palmatier (2017), corporate espionage is not easy to spot, especially since the primary purpose is to be off the radar. To uncover this kind of behavior, companies need advanced controls for monitoring data and endpoints.
The CPNI studies the multiple cases of insider threats that recognize the main activities, including five common activities as facilitating third party access to assets, process corruption, facilitating third party access, and IT disruption.
The commonly applied technique by insiders includes process corruption and disclosure of sensitive information to third parties (CPNI, 2013).
How to Reduce Internal Threat to the Business
Attacks on corporations do not come only through the internet. Insiders put privileged data at risk and are often driven by intentional actions. If the growing number of external attacks that IT professionals have to deal with is not enough, threats are being observed to incorporate internal environments.
Thus, adding security measures to the networks, capable of reducing cyber-attacks, are no longer sufficient. One must also be attentive to employees, especially those who have access to inside information, known as insiders.
A recent study, produced by the CSO in conjunction with the US Secret Service, showed that 29 percent of insider attacks resulted in more damage than malicious hacker damage.
The report also revealed that 47% of the company’s incidents were triggered by innocent employees, who eventually fell into data theft techniques such as phishing (Thompson, Ravindran, & Nicosia, 2015).
If it were only the innocence of these threats’ origin, it would require only obvious actions to resolve this type of occurrence, simply by continuing training and insistence on compliance with a Security Policy.
However, there are also malicious insiders. That is employees with access to privileged information.
Another survey, conducted by Yen, Lim, Wang, and Hsu, (2018), pointed out the main objectives of these bad employees who were caught. 62% of them were looking for a second source of income, conveying privileged data to competitors and the black market.
In comparison, 29% admitted to stealing information for future use, whether in other jobs in the same segment or even in personal initiatives. New companies and 9% assumed that they just wanted to sabotage the companies.
Hire an Expert Report Writer
Orders completed by our expert writers are
- Formally drafted in the academic style
- 100% Plagiarism-free & 100% Confidential
- Never resold
- Include unlimited free revisions
- Completed to match exact client requirements
The Immediate Response of the Supervisor
The supervisory authority only has to be notified of a breach of personal data if that breach presents risks to individuals’ rights and freedoms. In particular, it causes detrimental effects such as discrimination, reputation threat, financial loss, loss of confidentiality, or any other significant social or economic disadvantage.
This process has to be dealt with varies among different cases. For example, the supervisory entity will have to be notified about the loss of customer data when that loss places individuals at risk of identity theft (Haislip, Lim & Pinsker, 2017). Where the violation results in a high risk for individuals’ rights and freedoms, they will also have to be notified directly.
In this regard, a personal data breach must be reported to the supervisory body within 72 hours after the organisation knows of it. However, the RGPD allows this communication to be made in phases taking into account that it will most likely be impossible to investigate a data breach within this time frame (Thompson, Ravindran & Nicosia, 2015).
If the data breach is sufficiently serious to ensure its public disclosure, Inscriber Ltd., has to do the action without any delay. Failure to comply with these procedures means the application of fines is delayed. A login, for example, from a country where the company has no other unit can be considered a suspect. One of the newest techniques for identity theft is a denial of distributed services using misconfigured servers to perform amplification attacks.
Therefore, it is critical to verify that users are not contributing to creating the arsenals for the servers that can be used in attacks (Haislip, Lim & Pinsker, 2017). Ideally, the user themselves should be aware of the data that forms their identity and how much they are of interest to hackers. Companies must provide full support so that this information is not stolen by corporate networks, preventing attacks by its computers.
Protecting Employee Identity
It is important for the employee to fully aware of which of their data is open to being hacked by cybercriminals. Do a full name search on top search sites and enter phone numbers and documents, business, and home addresses to investigate what a malicious person can easily find on the internet.
Each employee should then receive training on how his/her routine browsing can impact the company’s business in which he/she works, even unconsciously; open attachments from unknown senders, click on malicious links, and other phishing possibilities (Trautman, & Ormerod, 2016). The IT staff should follow each user’s normal behavior, knowing the most common login and logout times, locations, and devices that he uses to connect to the system, and in case of any deviations from those standards, send an alert to security personnel.
Audit as an Anti-Corruption Tool
The audit constitutes a powerful weapon at the disposal of organisations to effectively combat corruption. The causes and not just the consequences of acts of corruption must be tackled. There is a myriad of audit techniques for detecting signs of corruption that are applied in Inscriber Ltd.
In the fight against corruption, the participation of all is fundamental. Reducing corruption is not an easy task; it will be up to each citizen to examine conscience to identify everyday situations that could be corrupted including attempted bribery in road blitz, acquisition of pirated products within the company (Thompson, Ravindran, & Nicosia, 2015). It is necessary to cut this risk to the Business because every policy is a mirror of its employee. Inscriber Ltd. management decides to involve auditing practices to ensure data security and protect business information to deal with this situation.
As a way to protect investors, several requirements are put to companies in this market. One is the choice of independent auditing. A company hired by a company interested in opening capital and should enjoy the freedom to scrutinize accounting and business practices (Yen, Lim, Wang, & Hsu, 2018). With this information that individuals, pension funds, and even other companies define their investments, being able to evaluate if the company is indebted, offers environmental risks that could generate protection.
This is used for recapitalizing the Business and consequently, devalues business actions. Haislip, Lim, and Pinsker (2017) indicated that without this information investors would not measure the risk to which they are exposing their money.
The audit stands out from the others from the available tools to minimize the risks of corruption in an organisation. With the advent of the Digital Public Bookkeeping System, institutions will have the best electronic audit software capable of crossing data to monitor and prevent fraud in real-time, and the on-site visit of the auditor is not necessary at the company’s headquarters.
Inscriber has applied this to clarify the Business’s improved process of control, improved control over the process, faster access to information, and more effective monitoring of cross-data operations (Suh & Yim, 2016). Therefore, it is Virtual Audit that has transformed business practices. The audit is facing new times: the virtual is already real, for inspection purposes.
Recommendation
58% of security incidents are caused by human errors, while technology failures cause only 42%. According to a recent study conducted by the Expert Security Company UK, almost one in five people have already been affected by workplace crime. It shows that internal threats must be given more and more attention from companies around the world. Here are some ways to make sure Business is not vulnerable to such threats:
Establish Security Policies
Companies need to ensure that data access is monitored in real-time. It is common to underestimate the impact that internal threats have on the corporate environment. Still, especially for privileged accounts, employees can have access to sensitive data and control the entire IT infrastructure. In this aspect, it is recommended that the company prevent internal threats to begin monitoring how their data is being used.
Organisations that do not have this kind of control of user access are unlikely to identify when they are misbehaving and block their actions. Over the past year, it has been found that each employee has access to 82% of the total 6.1 million folders incorporate systems (Wang, Gupta & Rao, 2015). About 28% of folders have universal access within companies – that is, everyone can access them without any kind of control over identity or activities within the files.
Introduce Robust Security Policies
More and more companies are now allowing their employees to use their own devices to work. The trend known as Bring Your Device (BYOD) requires companies to tailor their security strategy to this new reality. It is essential to introduce clear BYOD policies that specify what is allowed and what is not and offer appropriate training to the end-user.
Imagine, for example, that the HR director clicks on a phishing e-mail and suddenly a hacker has access to all of the HR data. It will be a major problem for the entire company, resulting from the leakage of personal data from employees and face several financial and reputational damages (Suh & Yim, 2016). Therefore, it is important to make sure everyone understands the dangers of data security and knows the right way to take advantage of BYOD to increase productivity while preventing internal threats.
Adequate Training
Providing the education necessary for the end-user to understand what is expected from him in terms of security will help ensure the entire Business’s protection. Therefore, it is important to communicate with the team, always with transparency, to maintain control before the situation leaves the managers’ hands.
By offering training with a few individual sessions, it will be possible to get to know employees better and build strong and lasting relationships, where individuals are encouraged to always strive for a balance between productivity and safety. Companies must create a culture that encourages employees to intelligently use corporate resources and stay away from illegal activities.
If you need assistance with writing your report, our professional report writers are here to help!
Conclusion
Based on the above discussion of customer data theft by internal employees, it has been concluded that insider threats are associated with people who have access to confidential information or an organisation’s private platforms that affect the business’s private information.
Moreover, it is conclusive to state that business management must be attentive to employees, especially those who access inside information. It has been found that attacks on corporations do not come only through the internet. Employees put privileged data at risk and are often driven by intentional actions.
References
BBC, 2007. Data lost by Revenue and Customs [Online] available at: http://news.bbc.co.uk/2/hi/uk/7103911.stm [Accessed on 14th Jan, 2019]
BBC, 2013. Hampshire policewoman Rebecca Swanston jailed for corruption [Online] available at: https://www.bbc.com/news/uk-england-hampshire-23548877 [Accessed on 14th Jan, 2019]
CPNI, 2013. CPNI INSIDER DATA COLLECTION STUDY [Online] available at: https://www.cpni.gov.uk/system/files/documents/63/29/insider-data-collection-study-report-of-main-findings.pdf [Accessed on 14th Jan, 2019]
Eberz, S., Rasmussen, K., Lenders, V., & Martinovic, I. (2015). Preventing lunchtime attacks: Fighting insider threats with eye movement biometrics.
Elhai, J. D., Chai, S., Amialchuk, A., & Hall, B. J. (2017). Cross-cultural and gender associations with anxiety about electronic data hacking. Computers in Human Behavior, 70, 161-167.
Haislip, J., Lim, J. H., & Pinsker, R. (2017). Do the Roles of the CEO and CFO Differ when it comes to Data Security Breaches?.
Janakiraman, R., Lim, J. H., & Rishika, R. (2018). The Effect of a Data Breach Announcement on Customer Behavior: Evidence from a Multichannel Retailer. Journal of Marketing, 82(2), 85-105.
Kammüller, F., & Probst, C. W. (2017). Modeling and verification of insider threats using logical analysis. IEEE systems journal, 11(2), 534-545.
Liu, L., De Vel, O., Han, Q. L., Zhang, J., & Xiang, Y. (2018). Detecting and Preventing Cyber Insider Threats: A Survey. IEEE Communications Surveys & Tutorials, 20(2), 1397-1417.
Martin, K. D., Borah, A., & Palmatier, R. W. (2017). Data privacy: Effects on customer and firm performance. Journal of Marketing, 81(1), 36-58.
Suh, Y. A., & Yim, M. S. (2016). A Feasibility Study on Detection of Insider Threats based on Human Bio-signals.
Thompson, N., Ravindran, R., & Nicosia, S. (2015). Government data does not mean data governance: Lessons learned from a public sector application audit. Government information quarterly, 32(3), 316-322.
Trautman, L. J., & Ormerod, P. C. (2016). Corporate Directors’ and Officers’ Cybersecurity Standard of Care: The Yahoo Data Breach. Am. UL Rev., 66, 1231.
Upton, D. M., and Creese, S., 2014. The Biggest Cybersecurity Threats Are Inside Your Company. RISK MANAGEMENT, The Danger from Within [Online] available at: https://hbr.org/2014/09/the-danger-from-within [Accessed on 14th Jan, 2019]
Wang, J., Gupta, M., & Rao, H. R. (2015). Insider threats in a financial institution: Analysis of attack-proneness of information systems applications. MIS quarterly, 39(1).
Yen, J. C., Lim, J. H., Wang, T., & Hsu, C. (2018). The impact of audit firms’ characteristics on audit fees following information security breaches. Journal of Accounting and Public Policy, 37(6), 489-507.
Zargar, A., Nowroozi, A., & Jalili, R. (2016, September). XABA: A zero-knowledge anomaly-based behavioral analysis method to detect insider threats. In Information Security and Cryptology (ISCISC), 2016 13th International Iranian Society of Cryptology Conference on (pp. 26-31). IEEE.
Frequently Asked Questions
To write a master’s level academic report:
- Define clear objectives.
- Conduct thorough research.
- Structure with sections like intro, methods, findings, discussion.
- Analyse critically.
- Incorporate evidence and references.
- Conclude and suggest further insights or research.





