Sample Undergraduate Computing Topic and Outline
Here is a sample that showcases why we are one of the world’s leading academic writing firms. This assignment was created by one of our expert academic writers and demonstrated the highest academic quality. Place your order today to achieve academic greatness.
Effective Cyber Security Strategies for the Internet of Things (IoT)
Introduction
In this modern and digital world, the Internet has implications for everything; it directly influences our lives; or indirectly impacts one or more aspects. With so many interlinked devices, instruments, and systems, the security and protection of information or data is a real concern today.
These concerns and ambiguities are resolved with implications of the Internet of things, but not well enough to rule out every threat. There are still breaches and gaps to fill. With computational intelligence (CI) tackling and managing cybersecurity challenges in the modern world, the Internet of Things and cyber-physical systems, cybersecurity concerns have a considerable role .
Internet of Things isn’t appropriate in every kind of circumstance. It has breaches and flaws concerning data theft, data security, personal data handling and securing from theft, and storage capabilities. Here, we will talk about practical strategies concerning Cybersecurity using the Internet of Things that make it better, safer, and trustworthy.
Keywords:
Cybersecurity challenges and Internet of Things, cybersecurity strategies
Literature review
Lee wrote and published his finding on the Internet of Things (IoT) cybersecurity; managing risks. He discussed concerns related to security and cyberattacks in maligning systems, collaborating devices, the network of machines, and organizations working with aligned systems.
He emphasized ever-increasing cyberattacks on the Internet of Things basis connected and aligned systems that harm individuals and organizations’ fame, reputation, commitments, failure to secure their financial dealings, and overall security operations. This has now become a usual thing and losing its credibility rapidly with growing trends of IoT devices, including monitoring systems, caretaking systems, manufacturing assistance systems, and automated logistics. With this drastic increase and spread of connectivity, it is easy to breach security barriers and steal what you want without letting the systems locate you.
Many researchers have admired and acknowledged the penetrating connectivity of devices among IoT channels, but its breach and vulnerability can never be ignored, especially with so much technological spread and far-reaching accessories. There is a need to bring about security and build the trust of individuals and organizations.
Methodology
A cyber risk management mechanism is built and conveyed with all its prerequisites to propose a reasonable and less vulnerable solution for tackling cybersecurity concerns, avoiding costly thefts and breaches of privacy. Our findings will help manage and achieve cost-effective security management by implementing a strategic and outbound secure environment. We employed the four-layered risk management plan for Cybersecurity and organized every aspect with every scenario to prevent breaches and losses.
Concluding remarks
Our research and findings have filled a gap in Cybersecurity. The strategic risk was tackling providing an ethical framework for using computational intelligence-based Internet of Things systems. With advancements and upcoming applications of 5G IoT services, there is a need to keep an eagle’s eye and monitor systems to will full potential so that you and your systems will feel secure every moment.
Hire an Expert Dissertation Topics and Outline Writer
Orders completed by our expert writers are
- Formally drafted in the academic style
- 100% Plagiarism-free & 100% Confidential
- Never resold
- Include unlimited free revisions
- Completed to match exact client requirements
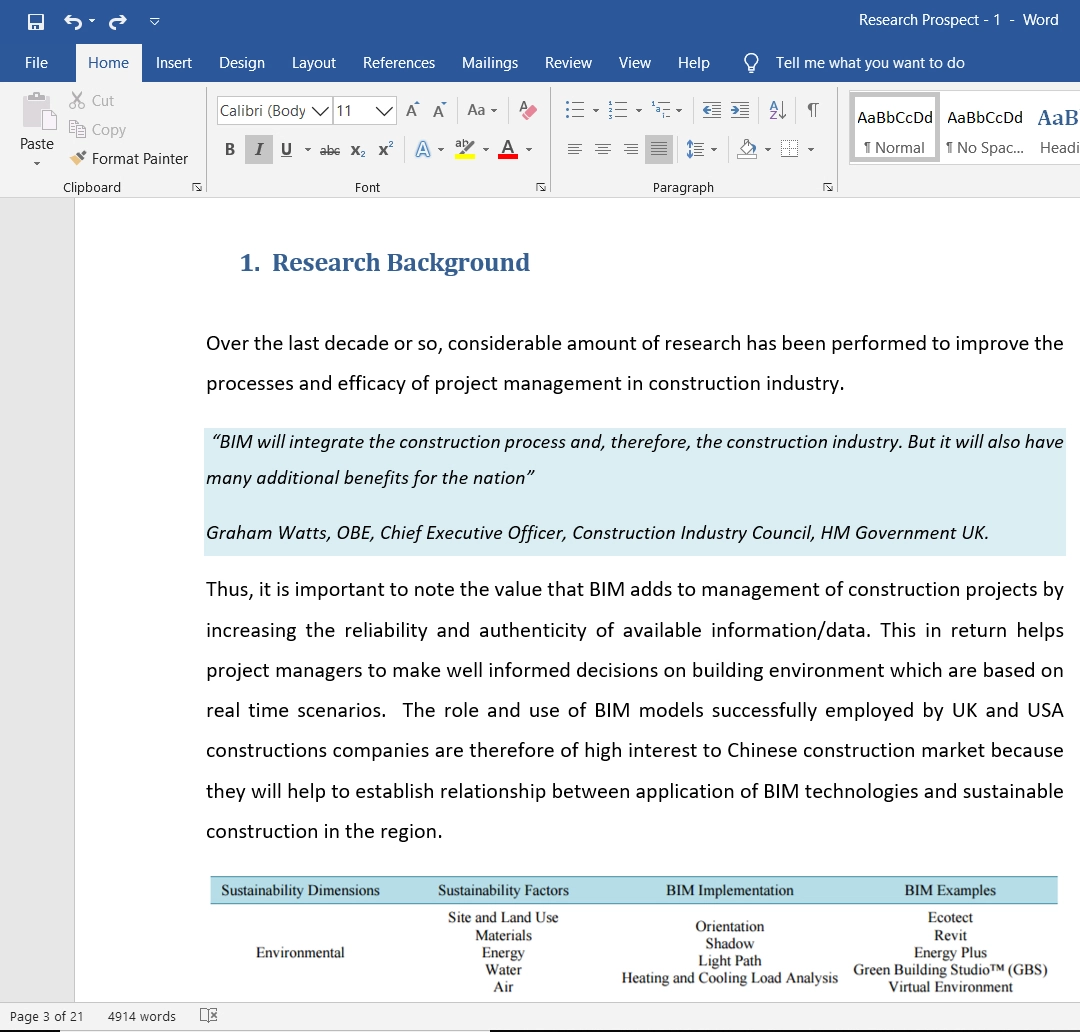
References
Akemi Takeoka Chatfield, C. G. R., 2019. A framework for the Internet of Things-enabled smart government: A case of IoT cybersecurity policies and use cases in U.S. federal government. Government Information Quarterly, 36(2), pp. 346-357.
Augusto-Gonzalez, J. et al., 2019. From the Internet of Threats to the Internet of Things: A Cyber Security Architecture for Smart Homes. Limassol, Cyprus, IEEE.
Dawson, M. E. M. O. M., 2016. Security Solutions for Hyperconnectivity and the Internet of Things. s.l.:IGI Global.
Huansheng Ning, H. L., 2012. Cyber-Physical-Social Based Security Architecture for Future Internet of Things. Advances in Internet of Things, Volume 2, pp. 1-7.
Juan Francisco Carías, L. L. J. M. S. J. H., 2019. Defining a Cyber Resilience Investment Strategy in an Industrial Internet of Things Context. Sensors, 19(1), p. 138.
Kyoung-Sik Min, S.-W. C. a. M. H., 2015. An International Comparative Study on Cyber Security Strategy. International Journal of Security and Its Applications, 9(2), pp. 13-20.
Lee, I., 2020. Internet of Things (IoT) Cybersecurity: Literature Review and IoT Cyber Risk Management. Future Internet, 12(9).
PetarRadanliev, D. C. D. R. R. N. M. H. R. M. M. S. C. P. B., 2018. Future developments in cyber risk assessment for the Internet of things. Computers in Industry, Volume 102, pp. 14-22.
Rolf H.Weber, E. S., 2016. Cybersecurity in the Internet of Things: Legal aspects. Computer Law & Security Review, 32(5), pp. 715-728.
Zhao, S., Li, S., Qi, L. & Xu, L. D., 2020. Computational Intelligence Enabled Cybersecurity for the Internet of Things. IEEE Transactions on Emerging Topics in Computational Intelligence, 4(5), pp. 666-674.
Frequently Asked Questions
To write an undergraduate dissertation outline, follow these steps:
- Define research objectives.
- Organize chapters & subtopics.
- Outline literature review.
- Plan data collection.
- Structure methodology.
- Create a timeline.
- Review and refine the outline.





